Scoping down access to specific entities
Using tags to restrict access
Consider the following scenarios:
- A large organization with multiple robotics divisions wants to use a unified system that their individual departments can leverage for their specific use cases. One department use case requires them to have a regional ops team to manage and operate the robot, while the other department specializes in selling their robots directly to the end user.
- A robotics startup wants to expose an app to their customers with real-time location, videos and metrics displaying the number of grapes picked by the robot.
- An OEM that manufactures robot arms and wants to provide a software to the distributors so that the distributors can provided enhanced features and support to their customers .
All of the above have one thing in common - scoping down access to the data from one organization to the next. Attribute-based access control (ABAC) is an authorization strategy that defines permissions based on attributes. At Formant, these attributes are called tags. You can attach tags to Formant resources. These tags will be used for matching conditions to grant permission to the users. Using tags to control access to your Formant resources, will allow your teams and resources to grow with fewer changes to policies.
Tags will be used to limit access to specific entities within resources. If a user access is scoped by tags, then the user can only access entities that have the same tag (within their role).
Rules to keep in mind
- If user has no tags, they can access all entities, within their role.
- If user has a tag, they can only access entities, within their role, with that tag.
- If user has multiple tags, they can only access entities that have all of the tags that the user has.
- If user that is assigned with ADMIN access policy is tagged, that user can only manage resources that has the same tag.
- If user is assigned "edit tag" capability, that user can manage access to resources that they have access to.
- Only custom roles can be assigned tags, default roles cannot be modified or assigned tags.
- Any user admin with the same tag as a role can assign the role to the users they manage.
- Tags in a team has two effects:
- Only users with the same tags can manage the teams
- Users in a team will inherit the tags applied to a team
- Any resource created by an admin with tags will inherit all the tags of that admin
In order to restrict access to certain entities, follow the steps below (in no particular order):
Step 1: Apply tag to the user or team
To apply tag to a user or team do the following:
- Click on the user's (or team's) name Settings ⇒ Users ⇒ <user's name>
- Choose Restrict Access tab
- Choose the tags that should be applied to the user and click SAVE
Step 2: Apply tag to the resource entities
Currently, Formant supports limiting access to the following resources:
- Devices
- Roles
- Views
To limit access to the corresponding resources, click on the corresponding resource entity under the Settings page and then choose the Tags section or tab under the entity and apply the tag.
As a general rule, roles are used to limit access to resources and tags are used to scope down the access to specific entities within that resource.
Example scenarios
Consider the following scenarios:
Scenario #1
- A large organization with multiple robotics divisions wants to use a unified system that their individual departments can leverage for their specific use cases. One department use case requires them to have a regional ops team to manage and operate the robot, while the other department specializes in selling their robots directly to the end user.
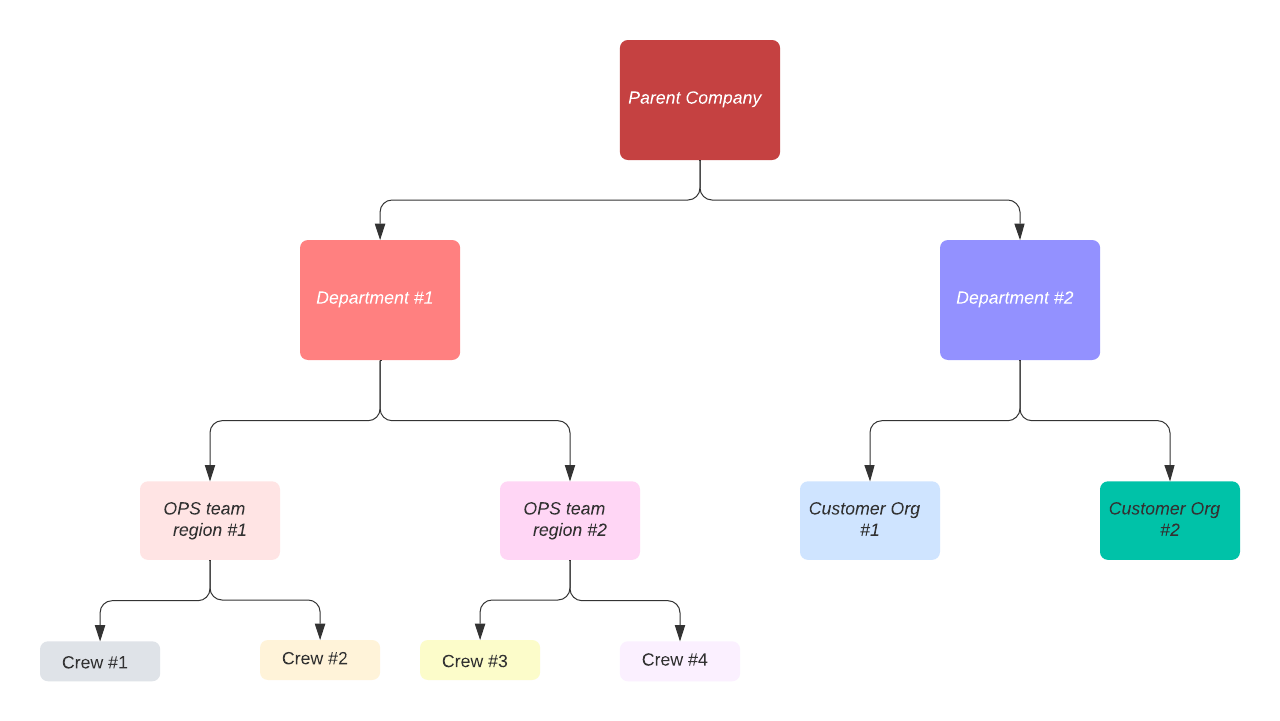
To accomplish the above scenario, the following steps have to be followed:
Parent Company Org admin does the following:
- Create and assign tag - dept-access:yes to all relevant devices and Views
- Create one custom role for administrators of Department #1 and Department #2
- The role is named sub-admins
- Assign ADMIN on resource user
- Assign EXECUTE with Edit tags enabled for views, roles and devices
- Assign EXECUTE on all other resources
- The role is assigned tags called dept-access:yes so that any user admin with these tags can assign this role to the users they manage.
- Create custom role for Viewers custom-viewers
- Assign VIEWER on all resources
- The role is assigned tags called dept-access:yes
- Create custom role for Operators custom-operators
- Assign EXECUTE on all resources
- The role is assigned tags called dept-access:yes
- Create team Department#1 team:
- Assign role sub-admins
- Assign tag dept-access:yes to the team
- Create and assign tag dept#1-access:yes to all the roles
- Assign tag dept#1-access:yes to the Department#1 team
- Assign tag dept#1-access:yes to the device and views relevant to this team
- Create team Department#2 team:
- Assign role - sub-admins
- Assign tag - dept-access:yes to roles, teams, devices and views
- Create and assign tag dept#2-access:yes to all the roles
- Assign tag dept#2-access:yes to the Department#2 team
- Assign tag dept#2-access:yes to the device and views relevant to this team
- Invite the first sub-admins of Department #1 and Department #2
The first administrator of Department #1 has to do the following:
- Create teams (Ops#1, Ops#2) for second-level sub-admins.
- The team inherits all the tags from Department #1 admin dept#1-access:yes, dept-access:yes
- Assign role sub admins
- Create tags ops1-access:yes and ops-2-access-yes and assign respectively to the team and to the custom-operators roles
- Assign tags ops1-access:yes and ops-2-access-yes to the respective devices and views
-Invite second-level sub-admins from Ops#1 and Ops#2 team
The first admins of Ops#1 and Ops#2 teams have to invite their Crew who are expected to operate the devices. This set of users only need to be able to assign custom-operator role to their users.
- Create teams (Crew#1, Crew#2, Crew#3, Crew#4) for the operator teams
- Create and assign the respective tags crew1-access:yes , crew2-access:yes , crew3-access:yes, crew4-access:yes to the team
- Assign role custom-operators to the teams
- Assign the respective tags to devices and Views
The first administrator of Department #2 has to do the following:
- Create teams (Cust#1, Cust#2) for customer-level sub-admins.
- The team inherits all the tags from Department #2 admin dept#2-access:yes, dept-access:yes
- Assign role sub admins
- Create tags cust1-access:yes and cust-2-access:yes and assign respectively to the team and to all the relevant roles
- Assign tags cust1-access:yes and cust-2-access:yes to the respective devices and views
- Invite second-level sub-admins from Cust#1 and Cust#2 team
The first administrators of Cust#1 and Cust#2 has to do the following:
- Invite team members to Formant
- Assign the relevant role to the invited team members
Scenario #2
- A robotics startup wants to expose an app to their customers with real-time location, videos and metrics displaying the number of grapes picked by the robot.
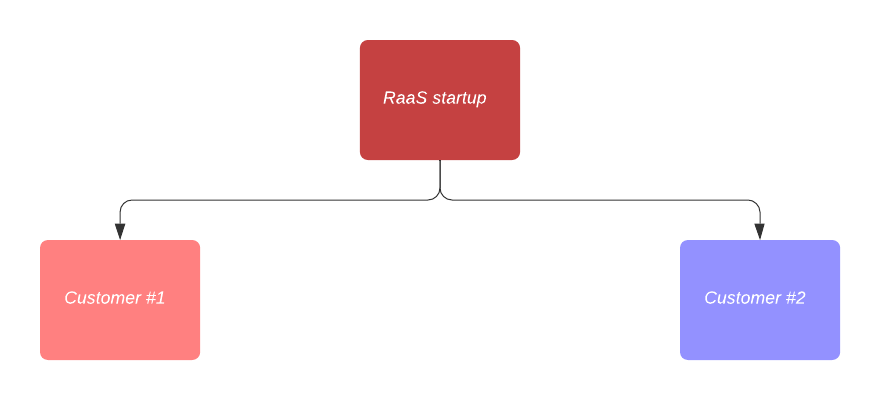
The RaaS organization administrator has to do the following:
- Create one custom role for administrators of Department #1 and Department #2
- The role is named sub-admins
- Assign ADMIN on resource user
- Assign EXECUTE with Edit tags enabled for views, roles and devices
- Assign EXECUTE on all other resources
- The role is assigned tags called cust1-access:yes and cust2-access:yes so that any user admin with these tags can assign this role to the users they manage.
- Create custom role for Viewers custom-viewers
- Assign VIEWER on all resources
- The role is assigned tags called cust1-access:yes and cust2-access:yes
- Create custom role for Operators custom-operators
- Assign EXECUTE on all resources
- The role is assigned tags called cust1-access:yes and cust2-access:yes
- Create teams (Cust#1, Cust#2) for customer-level sub-admins.
- Assign role sub admins
- Create tags cust1-access:yes and cust-2-access:yes and assign respectively to the team and to all the roles
- Assign tags cust1-access:yes and cust-2-access:yes to the respective devices and views
- Invite second-level sub-admins from Cust#1 and Cust#2 team
Scenario #3
- An OEM that manufactures robot arms and wants to provide a software to the distributors so that the distributors can provided enhanced features and support to their customers
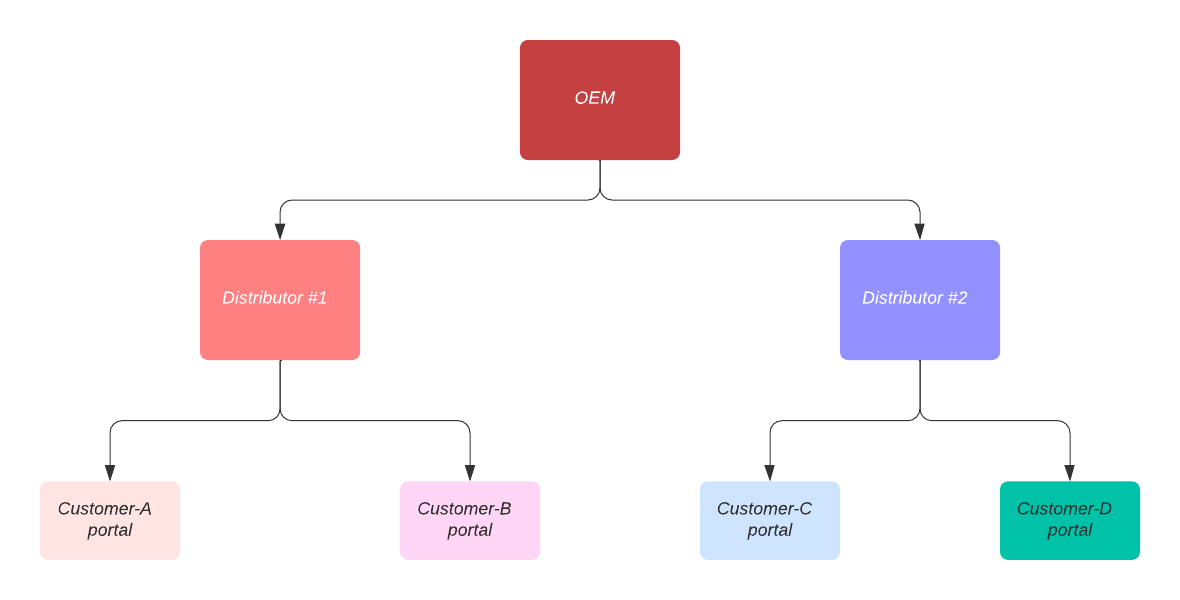
To accomplish the above scenario, the following steps have to be followed:
OEM Company Org admin does the following:
- Create and assign tag - dept-access:yes to all relevant devices and Views
- Create one custom role for administrators of Department #1 and Department #2
- The role is named sub-admins
- Assign ADMIN on resource user
- Assign EXECUTE with Edit tags enabled for views, roles and devices
- Assign EXECUTE on all other resources
- The role is assigned tags called dept-access:yes so that any user admin with these tags can assign this role to the users they manage.
- Create custom role for Viewers custom-viewers
- Assign VIEWER on all resources
- The role is assigned tags called dept-access:yes
- Create team Department#1 team:
- Assign role sub-admins
- Assign tag dept-access:yes to the team
- Create and assign tag dept#1-access:yes to all the roles
- Assign tag dept#1-access:yes to the Department#1 team
- Assign tag dept#1-access:yes to the device and views relevant to this team
- Create team Department#2 team:
- Assign role - sub-admins
- Assign tag - dept-access:yes to roles, teams, devices and views
- Create and assign tag dept#2-access:yes to all the roles
- Assign tag dept#2-access:yes to the Department#2 team
- Assign tag dept#2-access:yes to the device and views relevant to this team
- Invite the first sub-admins of Department #1 and Department #2
The first administrators of Department #1 and Department #2 has to do the following: - Create respective customer teams (Cust#A, Cust#B, Cust#C, Cust#d) for customer-level viewers.
- The team inherits all the tags from Department #1 and Department #2 admins
- Assign role custom viewers
- Create tags custA-access:yes, custB-access:yes, custC-access:yes and custD-access:yes and assign respectively to the team and to all the relevant roles
- Assign tags custA-access:yes, custB-access:yes, custC-access:yes and custD-access:yes to the respective devices and views
- Invite the respective user from customers and assign them to the right team
Updated about 2 years ago
